Page 43 - OctDefComp
P. 43
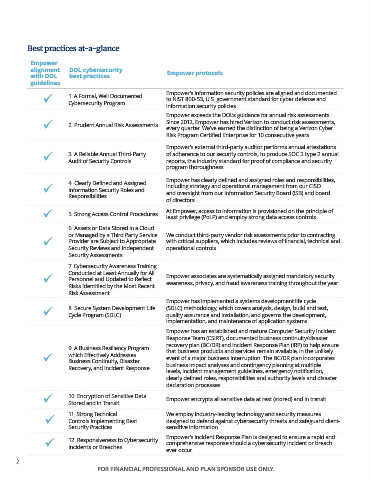
Best practices at-a-glance
Empower
alignment DOL cybersecurity Empower protocols
with DOL best practices
guidelines
Empower’s information security policies are aligned and documented
1. A Formal, Well Documented to NIST 800-53, U.S. government standard for cyber defense and
Cybersecurity Program
information security policies.
Empower exceeds the DOL’s guidance for annual risk assessments.
2. Prudent Annual Risk Assessments Since 2012, Empower has hired Verizon to conduct risk assessments,
every quarter. We’ve earned the distinction of being a Verizon Cyber
Risk Program Certified Enterprise for 10 consecutive years.
Empower’s external third-party auditor performs annual attestations
3. A Reliable Annual Third-Party of adherence to our security controls, to produce SOC 2 type 2 annual
reports, the industry standard for proof of compliance and security
Audit of Security Controls
program thoroughness.
Empower has clearly defined and assigned roles and responsibilities,
4. Clearly Defined and Assigned including strategy and operational management from our CISO
Information Security Roles and and oversight from our Information Security Board (ISB) and board
Responsibilities
of directors.
5. Strong Access Control Procedures At Empower, access to information is provisioned on the principle of
least privilege (PoLP) and employ strong data access controls.
6. Assets or Data Stored in a Cloud
or Managed by a Third Party Service We conduct third-party vendor risk assessments prior to contracting
Provider are Subject to Appropriate with critical suppliers, which includes reviews of financial, technical and
Security Reviews and Independent operational controls.
Security Assessments
7. Cybersecurity Awareness Training
Conducted at Least Annually for All Empower associates are systematically assigned mandatory security
Personnel and Updated to Reflect awareness, privacy, and fraud awareness training throughout the year.
Risks Identified by the Most Recent
Risk Assessment
Empower has implemented a systems development life cycle
8. Secure System Development Life (SDLC) methodology, which covers analysis, design, build and test,
quality assurance and installation, and governs the development,
Cycle Program (SDLC)
implementation, and maintenance of application systems.
Empower has an established and mature Computer Security Incident
Response Team (CSIRT), documented business continuity/disaster
recovery plan (BC/DR) and Incident Response Plan (IRP) to help ensure
9. A Business Resiliency Program that business products and services remain available, in the unlikely
which Effectively Addresses event of a major business interruption. The BC/DR plan incorporates
Business Continuity, Disaster
Recovery, and Incident Response business impact analyses and contingency planning at multiple
levels, incident management guidelines, emergency notification,
clearly defined roles, responsibilities and authority levels and disaster
declaration processes.
10. Encryption of Sensitive Data Empower encrypts all sensitive data at rest (stored) and in transit.
Stored and in Transit
11. Strong Technical We employ industry-leading technology and security measures
Controls Implementing Best designed to defend against cybersecurity threats and safeguard client-
Security Practices sensitive information.
Empower’s incident Response Plan is designed to ensure a rapid and
12. Responsiveness to Cybersecurity comprehensive response should a cybersecurity incident or breach
Incidents or Breaches
ever occur.
2
FOR FINANCIAL PROFESSIONAL AND PLAN SPONSOR USE ONLY.